The Power of Security Through Frequency
Ever get the sinking feeling you’ve left your keys at home, right when you need them most? Or maybe you’ve dealt with the frustration of a malfunctioning keycard? Thankfully, the world of access control is undergoing a revolution, leaving those worries behind. Access control credentials have evolved significantly over the decades, adapting to technological advancements while addressing security and convenience needs in various environments. This guide delves into the history, types of frequencies, applications, types of credentials, and practical scenarios, empowering organizations to make informed decisions about their security solutions.

A History of Access Control
The 20th century saw the introduction of magnetic stripe cards, a step forward in terms of convenience, but still prone to wear and tear. Then came the game-changer with proximity cards, which operate at 125 kHz frequencies eventually marked a significant advancement, enabling contactless authentication and reducing wear on physical cards. However, these early iterations were vulnerable to cloning and lacked robust security features.
The quest for enhanced security led to the rise of smart cards around the year 2000. In response to security challenges, higher-frequency smart cards emerged around the millennium, operating at 13.56 MHz. Frequency types, such as MIFARE®, revolutionized access control by incorporating cryptographic keys and secure data storage. They offer features like mutual authentication and secure messaging, creating an impenetrable shield against security breaches.
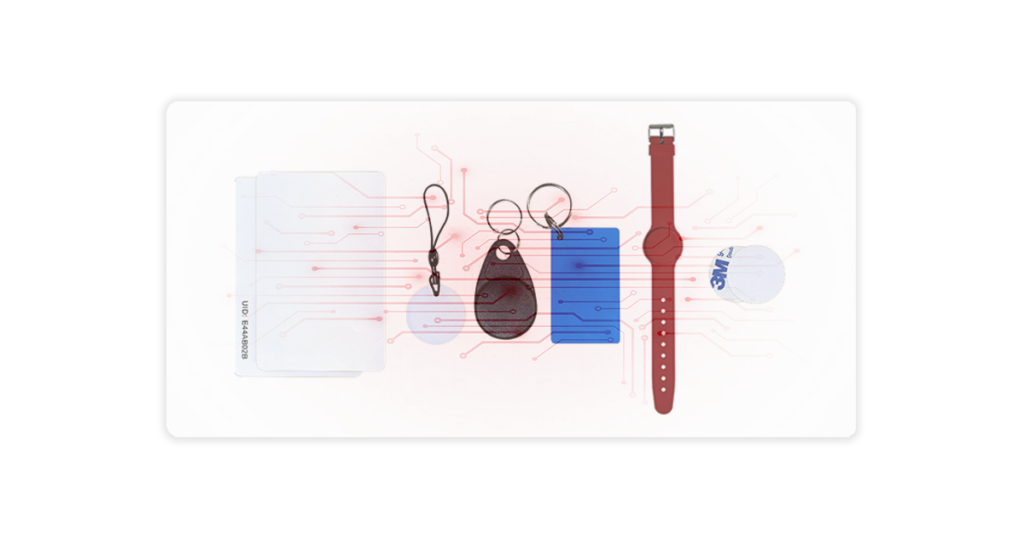
A Crew of Credential Choices
Today, the era of universal solutions has passed. Now, a diverse array of access control credentials offers unique strengths and capabilities for your security needs.
Key Cards
These versatile, traditional veterans are still popular for their customizability and ability to store data electronically. Key cards communicate with readers using RFID or NFC technology, offering a familiar and reliable solution that is versatile and can be customized with varying levels of security features.
Key Fobs
Small and portable, key fobs are perfect for those who prioritize convenience. Key fobs offer the same functionality as key cards but in a sleek, keychain-friendly form factor. They are popular for applications where users require convenient access without carrying bulky cards.
Coin Tags
These tiny, round stickers pack a mighty punch. Equipped with RFID or NFC technology, they offer a discreet access control solution. They offer flexibility in deployment and can be easily integrated into existing access systems.

Credentials Offer Benefits Beyond Convenience
While waving a key fob to unlock a door is undeniably cool, modern access control credentials offer a lot more than just convenience. Here’s why upgrading is a wise move:
Dedicated Security
Advanced encryption protocols and sophisticated authentication mechanisms make unauthorized access a near-impossible feat. These credentials act as guards, keeping intruders at bay and protecting your sensitive areas by utilizing advanced encryption and authentication mechanisms to protect against unauthorized access and cloning.
Unmatched Convenience
No more frantic searches for misplaced keys or fumbling with malfunctioning cards. Modern credentials offer effortless access through methods like tapping, waving, or even facial recognition. Contactless authentication reduces friction for users, enhancing operational efficiency.
Scalability for Growth
As your business expands, your access control system needs to keep up. Modern credential systems solutions are designed to accommodate growing organizational needs scalable, allowing you to easily add new credentials as your team grows. No need for a complete system overhaul – just integrate new members seamlessly.
Real-World Examples: Credentials in Action
Consider a scenario where a multinational corporation uses smart cards with MIFARE DESFire EV3 technology (13.56 MHz) to secure access to its headquarters. These advanced cards offer robust multi-application support and secure data storage, ensuring compliance with the strictest security protocols.
On the other hand, a university campus might leverage cost-effective proximity key fobs (operating at 125 kHz) to grant students access to dormitories and classrooms. These fobs provide a user-friendly and cost-effective solution for a large and dynamic user base.
Knowledge is Power in Access Control
Understanding the evolution, types, and applications of access control credentials empowers you to make informed decisions. By leveraging modern technologies and tailored solutions, businesses can mitigate security risks effectively while improving operational efficiency and user experience. With this knowledge, you can create a robust security system that keeps your facilities safe and your users happy. So, it might be time to get rid of those outdated key rings and keycards, and embrace the future of access control! A future filled with convenience, top-notch security, and a crew of credential companions ready to serve your needs.

